An app called 2FA Authenticator recently appeared on the Google Play Store, promising "secure authentication for your online services," boasting some features that are said to be missing from existing authenticator apps, such as proper encryption or backups. The problem was that it contained a dangerous banking trojan. Pradeo, a cybersecurity company, found this out.
The app also tried to convince users that it could import the authentication protocols of other two-factor authentication apps, namely Authy, Google Authenticator, Microsoft Authenticator, and Steam, and host them in one place. It also offered support for the HOTP (hash-based one-time password) and TOTP (time-based one-time password) algorithms.
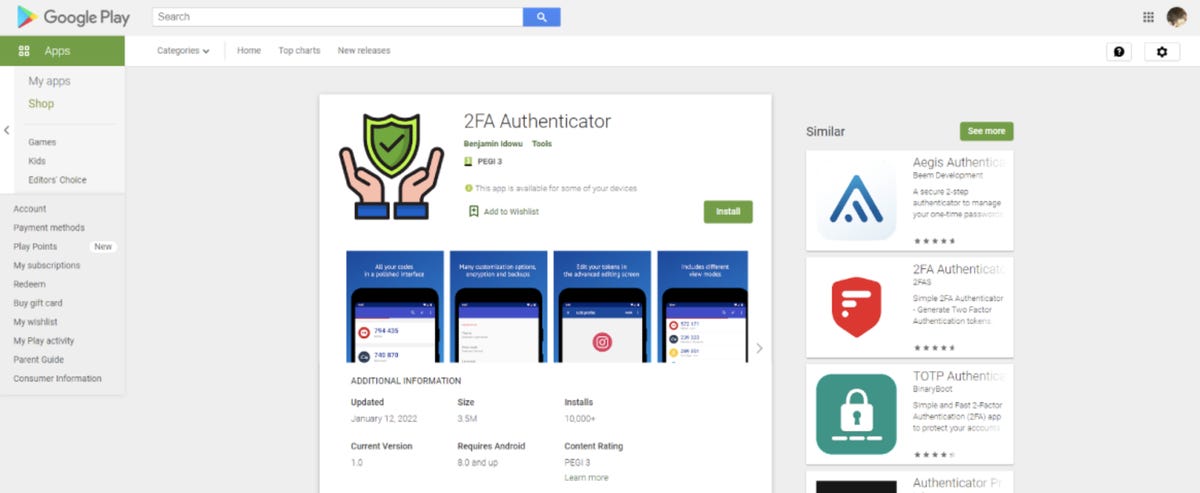
However, in reality, 2FA Authenticator was not intended to protect user data, but rather to steal it. According to Pradeo's experts, the application functioned as a so-called dropper for malware designed to steal financial data. It contained the open source code of the Aegis Authenticator application infected with malware.
After the app obtains the required permissions from the user, it installs the Vultur malware on their device, which can use screen recording and keyboard interaction recording to discover mobile banking passwords and login details for financial services (including cryptocurrency storage platforms).
The app has already been removed from the Google Store. However, in the 15 days it was available there, it recorded over 10 downloads. If you are one of those who have it on your phone, delete it immediately and change all important passwords to be safe.
You could be interested in