Google released Android 13 only a few days ago, but already hackers have focused on how to bypass its latest security measures. A team of researchers has discovered malware in development that uses a new technique to evade Google's new restrictions on which apps can access accessibility services. Abuse of these services makes it easy for malware to trace passwords and private data, making it one of the most used gateways for hackers to Androidu.
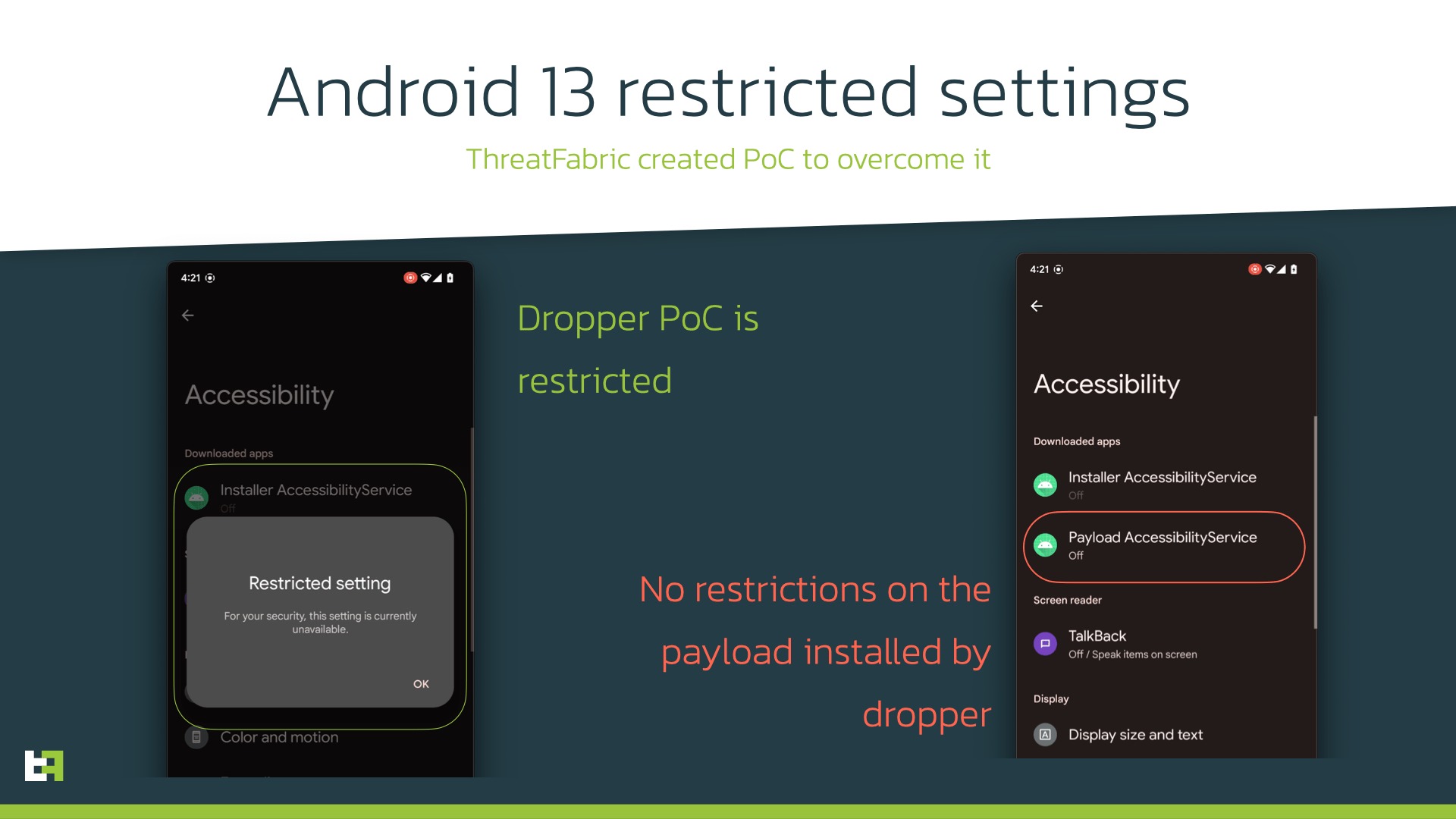
To understand what's going on, we need to look at the new security measures that Google is putting in place Androidu 13 implemented. The new version of the system no longer allows sideloaded apps to request accessibility service access. This change is meant to protect against malware that an inexperienced person might have inadvertently downloaded outside of the Google Play Store. Previously, such an app would have asked for permission to use accessibility services, but now this option is not as readily available for apps downloaded outside of the Google Store.
Since accessibility services are a legitimate option for apps that genuinely want to make phones more accessible for users who need them, Google doesn't want to ban access to these services for all apps. The ban does not apply to apps downloaded from its store and from third-party stores such as F-Droid or the Amazon App Store. The tech giant argues here that these stores usually vet the apps they offer, so they already have some protection.
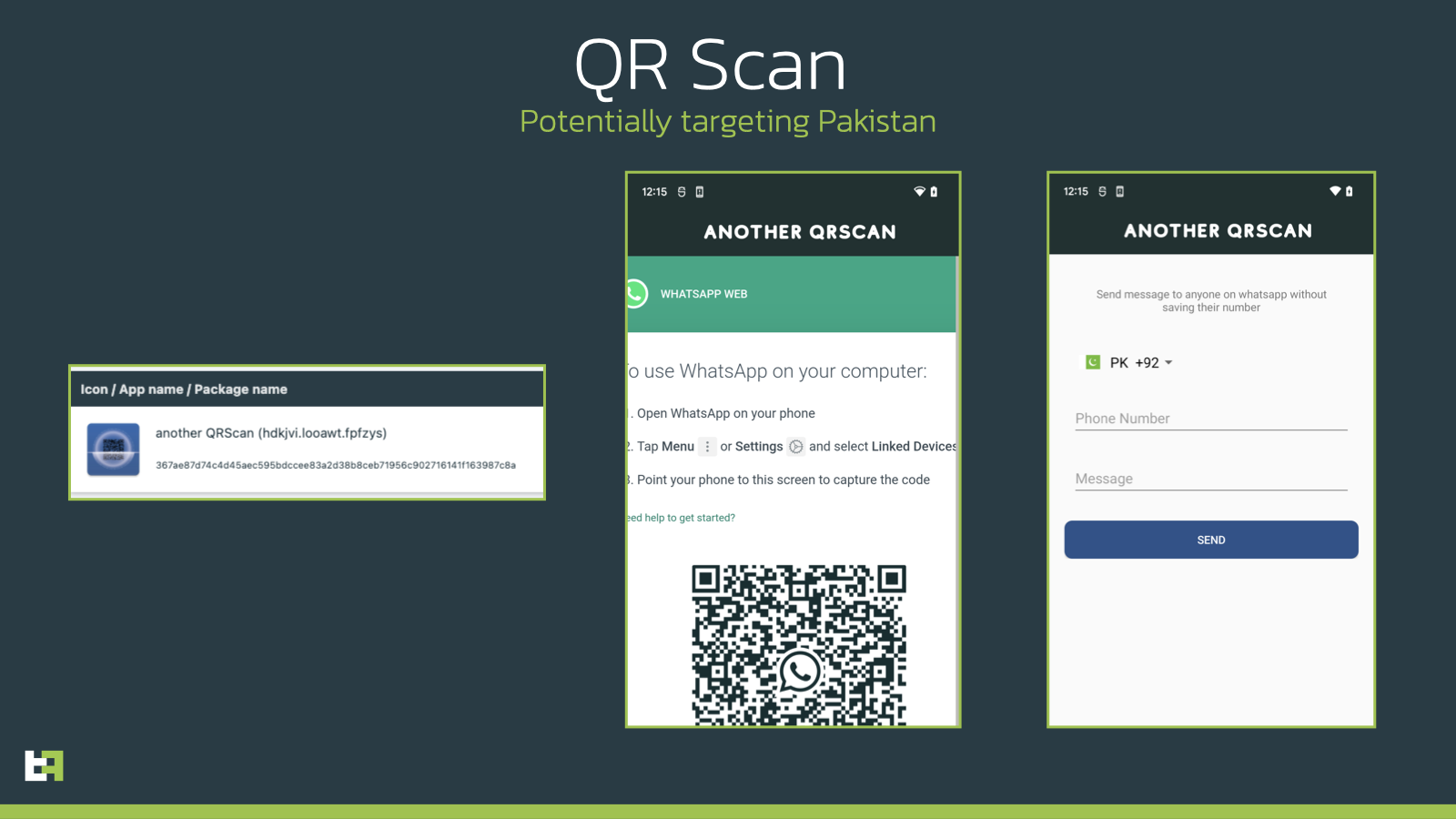
As a team of security researchers found out ThreatFabric, malware developers from the Hadoken group are working on a new exploit that builds on older malware that uses facilitation services to gain access to personal data. Since granting permission to apps downloaded "sideways" is v Androidu 13 harder, the malware consists of two parts. The first app that a user installs is a so-called dropper, which behaves like any other app downloaded from the store and uses the same API to install packages to then install "real" malicious code without the restrictions of enabling accessibility services.
You could be interested in

While the malware could still ask users to turn on accessibility services for sideloaded apps, the solution to enabling them is complicated. It's easier to talk users into activating these services with a single tap, which is what this double whammy accomplishes. The team of researchers notes that the malware, which they have named BugDrop, is still in the early stages of development and that it is currently heavily "bugged" itself. The Hadoken group previously came up with another dropper (called Gymdrop) that was also used to spread malware, and also created the Xenomorph banking malware. Accessibility services are a weak link for these malicious codes, so whatever you do, don't allow any app to access these services unless it's an accessibility app (with the exception of Tasker, a smartphone task automation app).