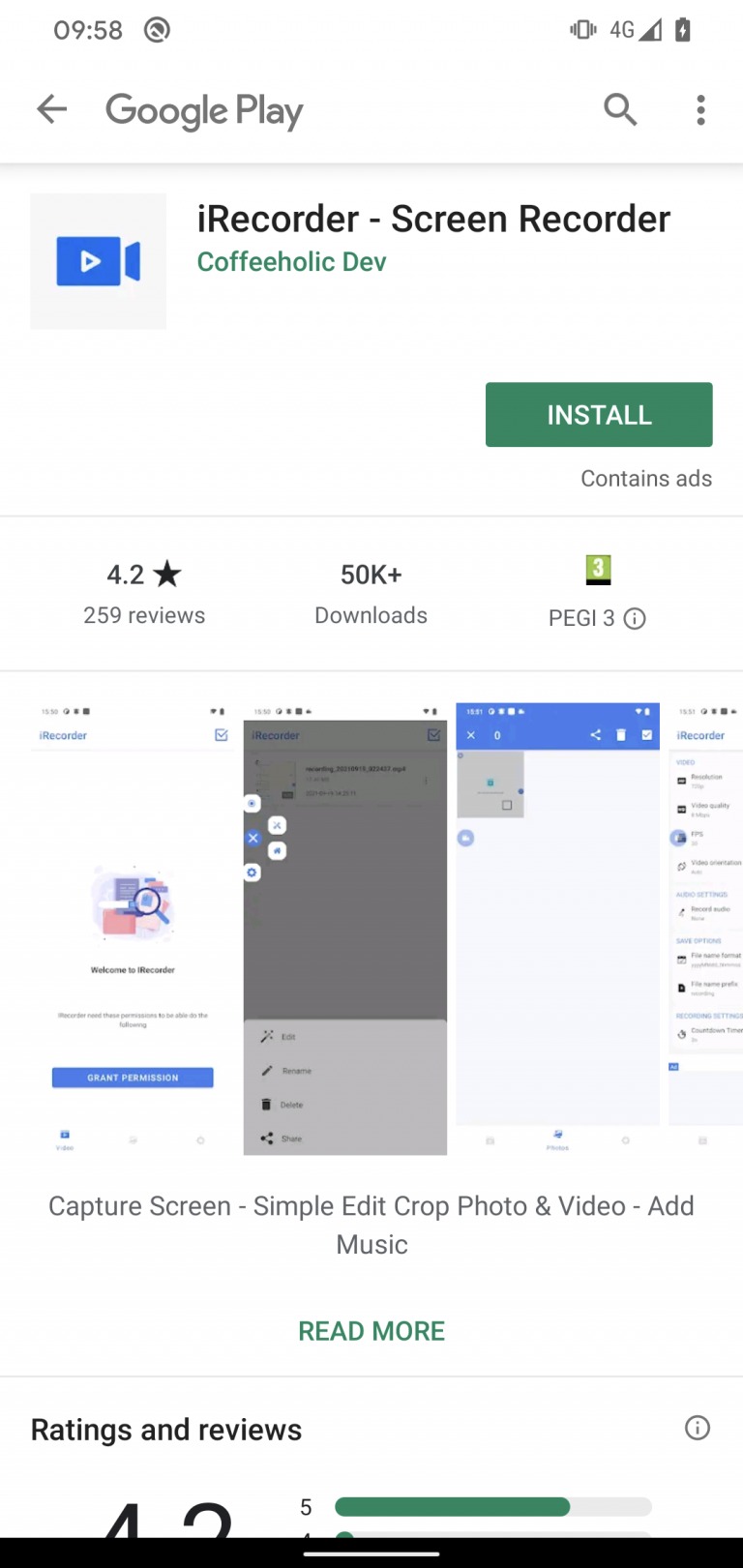
The popular app, which had more than 50 downloads on the Google Play Store, secretly recorded the surrounding audio every 000 minutes and sent it to its developer. This was discovered by a security researcher from ESET.
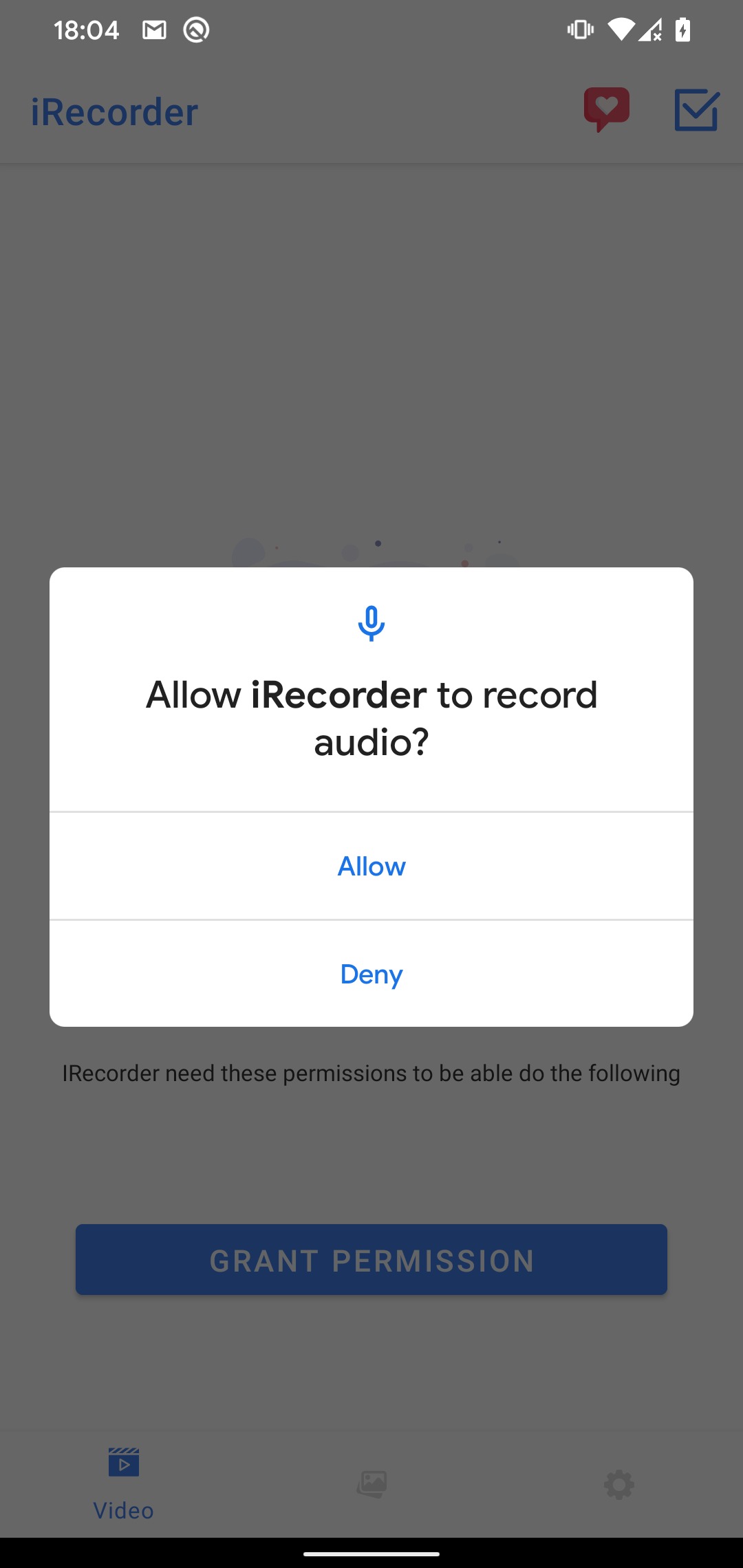
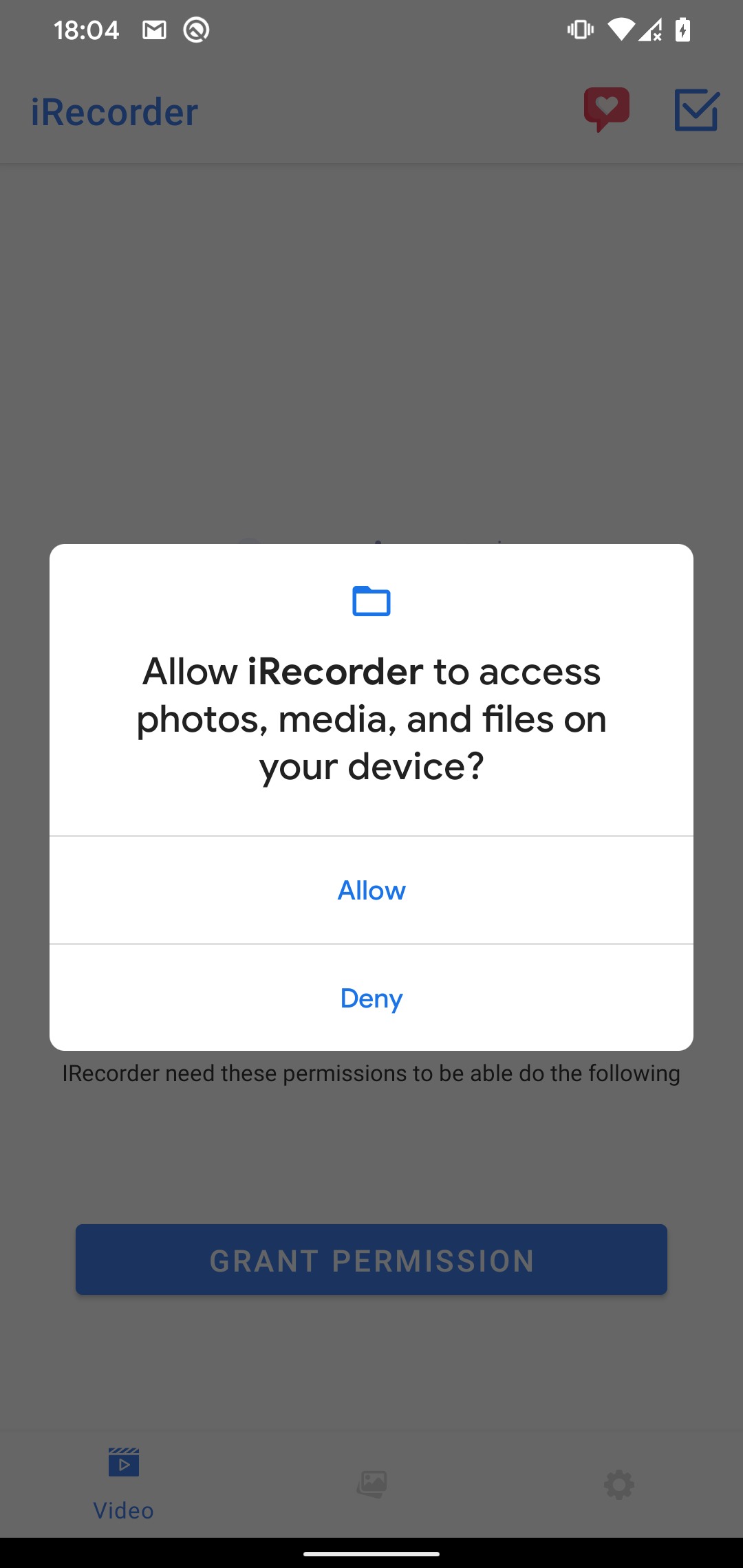
Application iRecorder Screen Recorder appeared on the Google Play Store in September 2021 as a harmless "app" that allowed users to record their screen androiddevices. Eleven months later, the app received an update that secretly added a brand new feature to it - the ability to remotely turn on the device's microphone and record audio, connect to a server controlled by the attacker and record audio and other sensitive files that were stored on the device. On blog this was stated by its researcher Lukas Stefanko to the cyber security company ESET.
The secret spying feature was introduced into iRecorder Screen Recorder using code from AhMyth, an open source RAT (Remote Access Trojan) that has been implemented into several other androidof applications. Once the RAT was added to iRecorder, all users of the previously harmless app received updates that allowed their devices to record nearby audio and send it to a server designated by the developer via an encrypted channel. The code taken from AhMyth has been heavily modified over time, which Stefanko says suggests the developer has become more adept at using the remote access trojan.
You could be interested in

Malware contained in applications offered in the Google store is nothing new. The US tech giant never comments on when malicious code is discovered in its store, only saying it will remove malware as soon as it is learned from outside researchers. Notably, he never explained why his own experts and automated scanning process fail to catch malicious apps discovered by strangers. Anyway, if you have the iRecorder Screen Recorder app, which has since been removed from the Google Store, on your phone, delete it immediately.






So we should immediately delete WhatsApp, which also listens in the background and all meta applications
Totally agree and google is not far behind.
What if you could also provide detailed instructions on how to delete applications when you're already writing about deleting them? In my opinion, a complicated and lengthy deletion is unnecessary, and in the vast majority of cases, a simple quick and simple uninstall is enough, but since you're writing about deletion, you should explain how it can be done.
I feel like throwing my mobile phone into the pond. The golden days when there were only phone booths and no internet. Children ran outside and now they sit at home with computers, and it's a miracle to meet a group of children outside. In addition to the eavesdropping, I want to add that I was not surprised. Who owns a mobile phone , which nowadays everyone, the system, knows everything about him (us).